We live in a world where security breaches and data losses are expected. According to a study done by IBM Security and the Ponemon Institute, the average cost of a data breach (from a sample of 500 companies interviewed) is $3.86 million. Moreover, mega data breaches, which result in the loss of 1 million to 50 million records, can cost a company $40 million to $350 million.
This makes it very hard to operate a company or even a single computer without a firewall. Here are a few ways to calculate the size of the firewall you’ll require to protect your data and safeguard your privacy.
There are myriad firewall options available around the world, and companies across the globe are working on their versions of security measures depending on what the most pressing issues are in the region. Some factors to consider may be the amount of traffic the firewall will see and the desired features you require.
Features
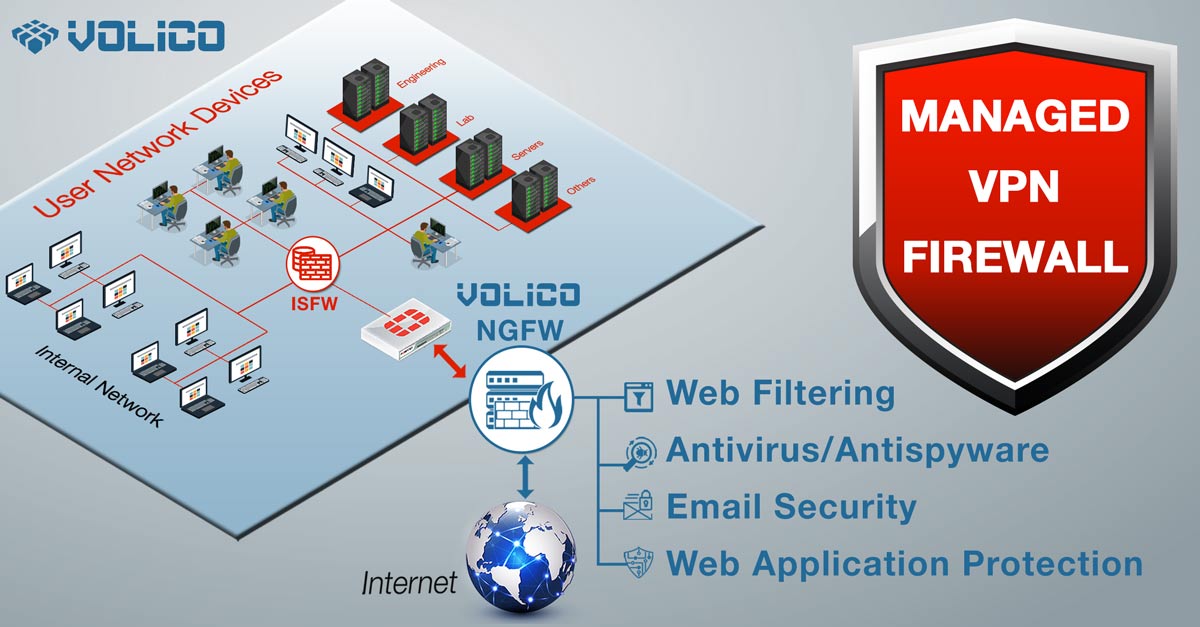
Next-Generation Firewalls have features such as application control, intrusion prevention, and content filtering that significantly improve the capacity of an administrator to monitor and control a network. But these services are often part of a subscription; sometimes, if you don’t need them, it doesn’t make sense to pay for them for no reason.
The advancements made in NGFW, from traditional firewalls, are numerous. The first addresses a significant flaw in TFW, offering inspection of layers two through seven. As a result, the administrator has more granular control over policies. Another major difference is application awareness. Rather than relying on preset links between applications and ports, the NGFW makes no assumptions and checks all traffic. This closes a significant loophole that had previously allowed some malware to slip through. The way in which Next-Generation Firewalls assesses the identity of the data packets is also different from TFW, relying on LDAP or Active Directory.
This is an improvement on previous iterations that made it more challenging or impossible to differentiate between various users’ permissions and access. NGFW also employs a fully integrated intrusion protection system, whereas TFWs utilizes a discrete appliance. Finally, NGFW also allows users to use either bridged or routed modes, allowing them to interact with sites that still employ TFW.
However, consult with your security provider first; subscription packages often contain automatic anti-virus updates that are of great use.

Sizing a Firewall
This goes beyond considering features. There are two ways to size a firewall in most cases, user count and throughput.
User Count measures the total devices that can access a single firewall simultaneously. This is different from the average amount of users on a network at the same time. This is also different from the employee count since the focus should be on the customers and users instead.
In the case of internet-facing servers, companies should be wary of the total users accessing the internet at one time and not rely on an average for their firewall. If the servers are overloaded, that’s the same as a DDoS attack.
Throughput deals with the speed of the traffic that passes through the firewall. Firewalls usually have ratings for speeds listed in their specifications. They can’t speed up your internet connection; they can only provide a bottleneck. For instance, a firewall of 75 Mbps will slow down your gigabit internet connection to that speed; it simply can’t allow that much traffic.
 Real-Life Examples
Real-Life Examples
Fortinet FortiGate-100D is rated for 300 Mbps, runs proxy-based Anti-virus software, and has a maximum user count of 150. However, the same firewall can handle 1.5 Gbps without any bells and whistles, but that’s not a good deal in the long run.
Other services like Sophos and Cisco offer similar packages to handle traffic and place restrictions on user counts.
You can opt for any one of these services or the multiple services not mentioned in this piece. However, know that the more you know about firewalls, the better equipped you can make an informed choice.
Why have my Firewall Managed by Volico?
Firewall management is an ongoing process that requires IT security expertise, and having a poorly configured firewall is like not having a firewall. Firewalls continue to be a great first line of defense in your cybersecurity strategy. However, ongoing management of the devices can be time-consuming and resource-intensive. Our certified engineers can take over the everyday management tasks so your team can focus on more strategic business issues.
Discuss your firewall security protection needs with experienced IT representatives
High-quality firewall security is a must. One breach can cause lost revenue, lost consumers, and significant downtime. Firewalls should be able to handle a broad range of malicious attacks and continuously be aware of new ones. To discuss your firewall protection needs with a skilled data center representative, don’t hesitate to contact us.
Discover how Volico Data Centers can help you with your Managed Security needs.
• Call: 305-735-8098
• Chat with a team member to discuss which solution best fits your needs.






 Real-Life Examples
Real-Life Examples